ch 7
P.M.A CH 7
In this lab we have a samble with some questions to be answerd let’s just open it an start our analysis and find some answers
start
opening IDA IDA Freeware and droping our file into it then we find a dialog window then the file opens
Lab 7-1
1. How does this program ensure that it continues running (achieves persistence) when the computer is restarted?
From main we find only one subrotine call (sub_401040)
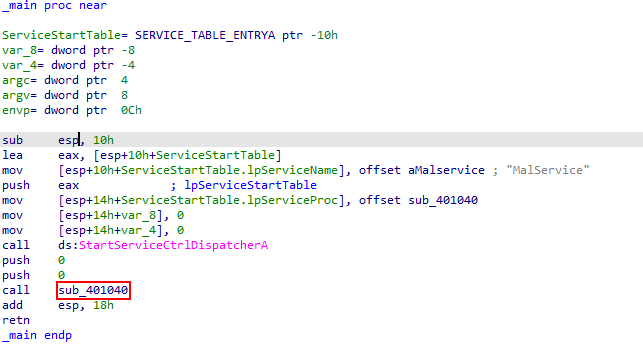
diving in this subrotine found the first indicator (OpenSCManagerA) which is an API Establishes a connection to the service control manager on the specified computer and opens the specified service control manager database. then found (CreateServiceA) Creates a service object and adds it to the specified service control manager database. until now there is nothing to persistence but on searching for documentation of this functioin found that one of it’s Parameters is dwStartType which indicate start option that one was passed with value 0x2 which stands for auto start.
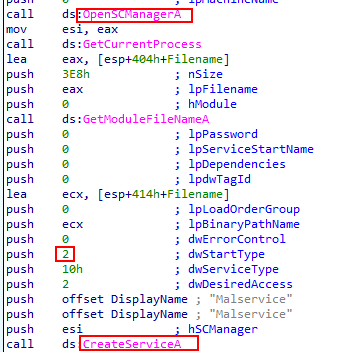
2. Why does this program use a mutex?
from the same subrotine we find another call to OpenMutexA which Creates or opens a named or unnamed mutex object.
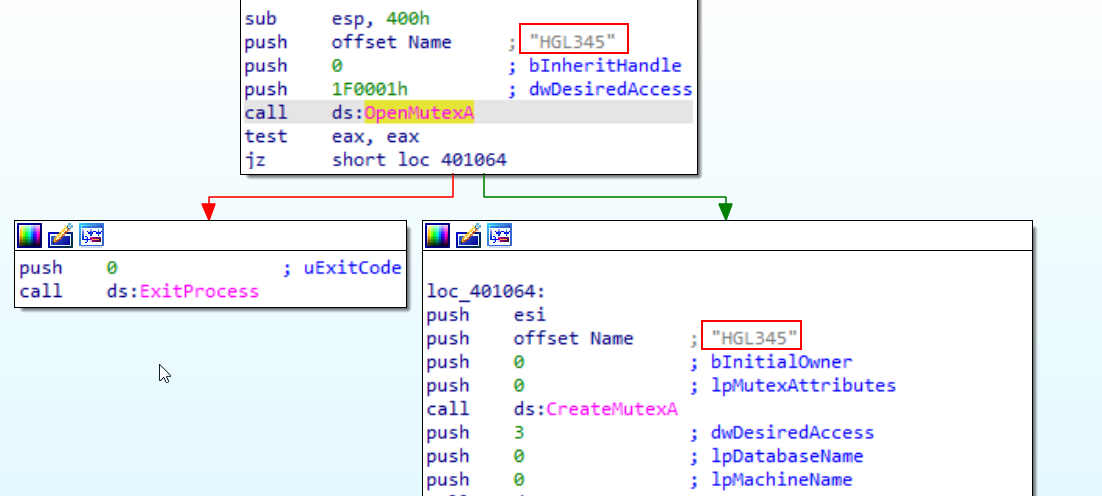
here we find that first it tries to open mutex “HGL345” then if it exsist the program terminates else it creat one with this name so it’s obvious that it’s a chick for existence of another copy of malware runnig
3. What is a good host-based signature to use for detecting this program?
we could use the “HGL345” mutex mentioned previously as it’s a unique one created with htis malware
4. What is a good network-based signature for detecting this malware?
After looking at the created service there some calls make sense together
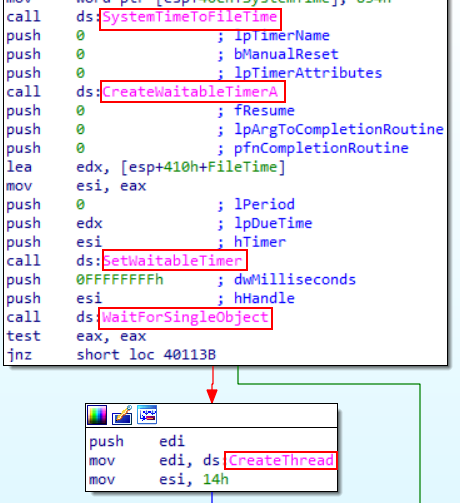
first SystemTimeToFileTime Converts a system time to file time format. System time is based on Coordinated Universal Time CreatWaitableTimerA which creates or opens a waitable timer object SetWaitableTimer activates the specified waitable timer. When the due time arrives, the timer is signaled and the thread that set the timer calls the optional completion routine WaitForSingleObject Waits until the specified object is in the signaled state or the time-out interval elapses so from these call we can conclude that before first call the time was set to 834h which referes to first of January / 2100 at midnight then creat a timer that wait until this date and then creat a thread on thread activation it start in loop
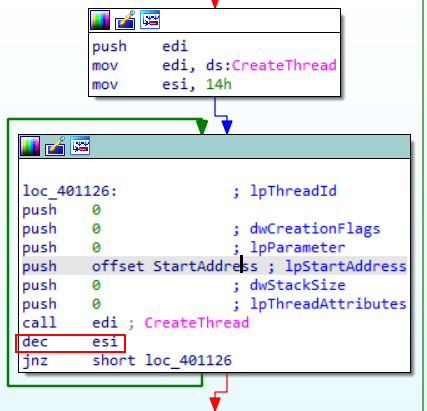
the loop start with esi as counter set to 14h which means 20D that means the loop will be repeated 20 times as the esi is decremented every time the loop creat thread that take an important prameter which is ip start address on chicking that offset found that malware uses “Internet Explorer 8.0” to go to “http://www.malwareanalysisbook.com” which is our network based signature.
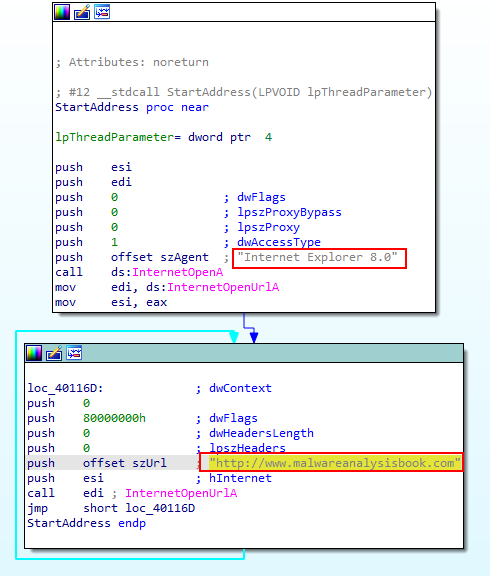
5. What is the purpose of this program?
from mentioned previously the program waits until 1/1/2100 then starts to send infinite number of requests to that website to make server collapse which called DOS-Attack
6. When will this program finish executing?
That program will last to infintiy once starting at 1/1/2100 midnight
Lab 7-2
1. How does this program achieve persistence?
On checking main code there is no any indicator that say the program achieve persistence, it runs once and end.
2. What is the purpose of this program?
On the analisys first, it initializes COM and obtain a pointer to a COM object with OleInitialize & CoCreateInstance.
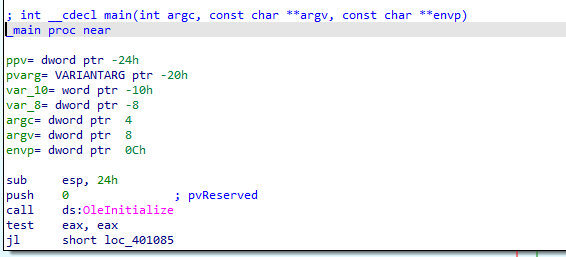
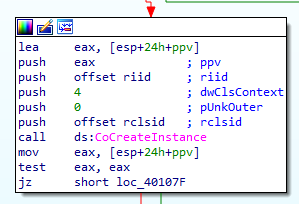
looking at passed parameters to CoCreateInstance we found iid & clsid checking those offsets found
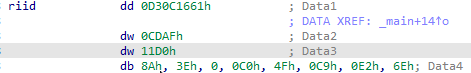
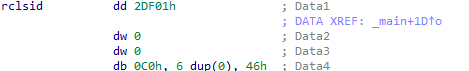
By concatenating those we found iid : D30C-1661-CDAF-11D0-8A3E-00C0-4FC9-E26E clsid : 0002-DF01-0000-0000-C000-0000-0000-0046 searching for those ids found that class id is for Internet Explorer and IID is for WebBrowser2
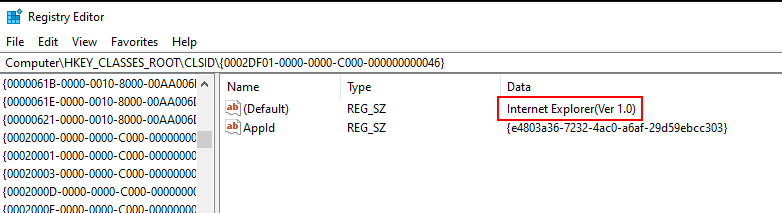
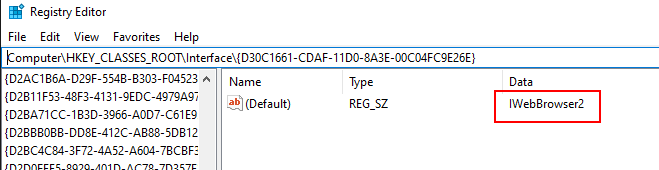
After that the CoCreateInstance returns com object at location stored at eax then eax is dereferenced and edx points to the beginning of the com object itself
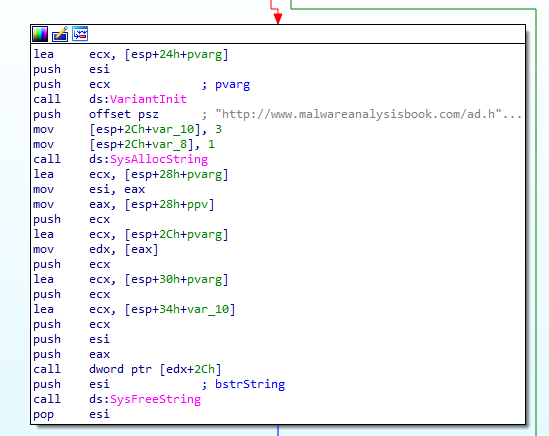
then InternetExplorer navigates to the web address ‘http://www.malwareanalysisbook.com/ad.html’ then some cleaning and poping habbens then the program terminate
So as conclusion the program runs one time opening html page then terminate without modifing any thing at system
3. When will this program finish executing?
After desplaing the html page
Tools used :
- IDAFREE-7.7