ch 5
P.M.A CH 5
In this lab we have a samble with some questions to be answerd let’s just open it an start our analysis and find some answers
start
opening IDA IDA Freeware and droping our file into it then we find a dialog window then the file opens
on opening a file the AI of ida recognise the main function under name DLLMain(x,x,x)
What is the address of DllMain?
here it’s better to use text view so we find our address is simply 1000D02E
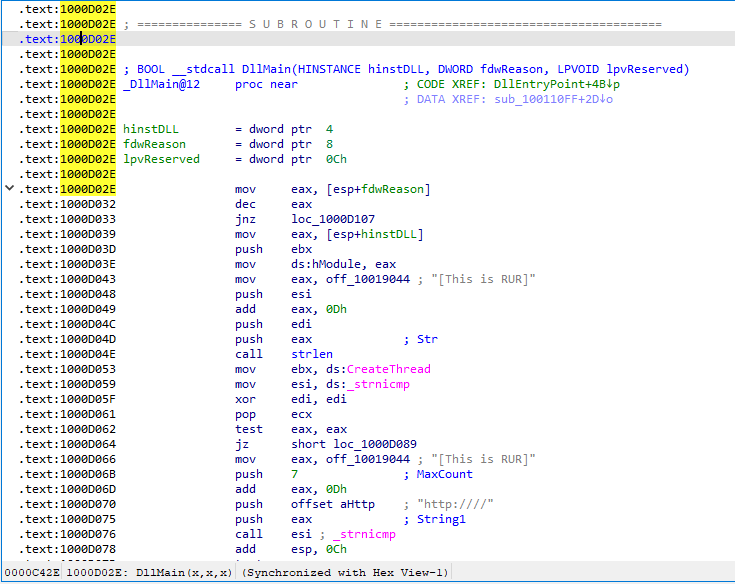
Use the Imports window to browse to gethostbyname. Where is the import located?
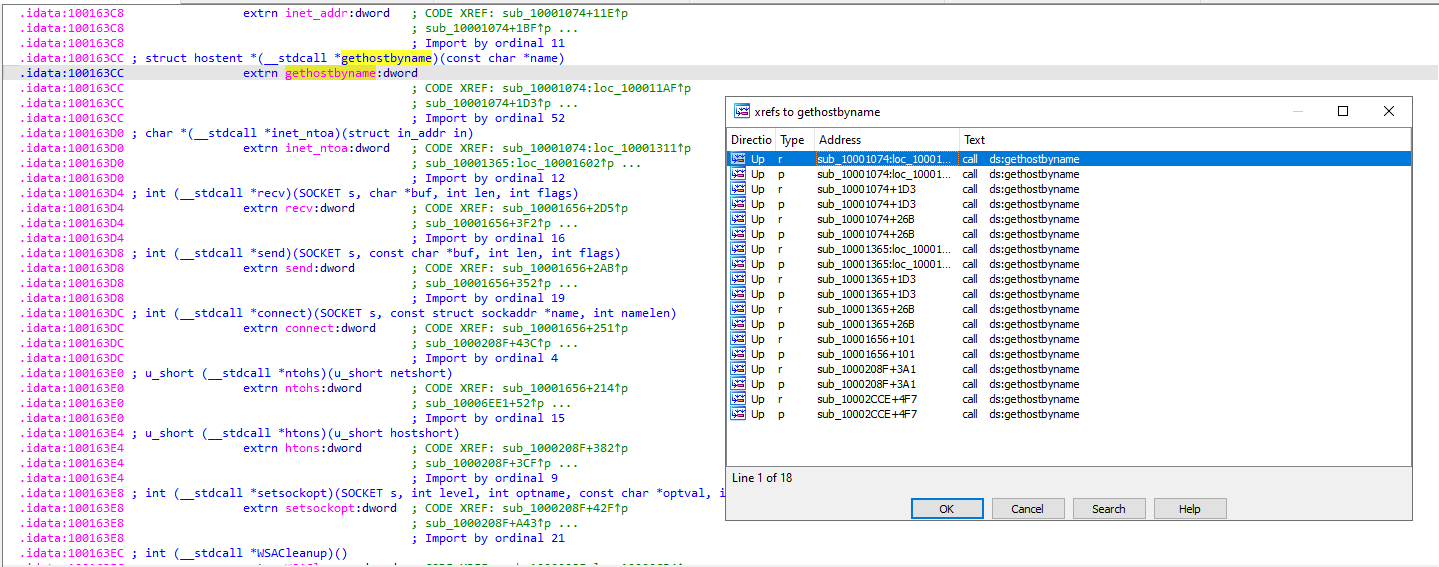
opening imports tab then pressing ALT+T it opens search by string then entering gethostbyname we easly reach to our import and find address is 100163CC

How many functions call gethostbyname?
Double-clicking on gethostbyname it opens in assembly code then using Xref table (CTRL+x) we find it was called 18 times by 5 functions.
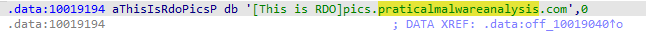
Focusing on the call to gethostbyname located at 0x10001757, can you figure out which DNS request will be made?
on jumping to address we found function call so go upside to check the arguments passed to this call
on checking found that off_10019040 is stored in eax on going to this off set found that website stored praticalmalwareanalysis.com
How many local variables has IDA Pro recognized for the subroutine at 0x10001656?
Jumping to address we find that 23 variable.
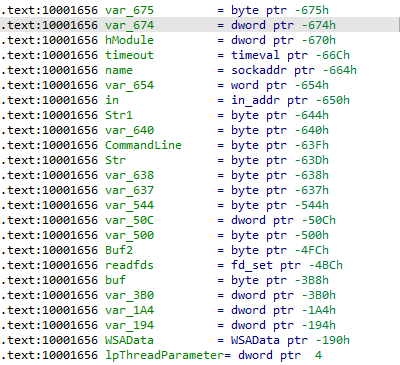
How many parameters has IDA Pro recognized for the subroutine at 0x10001656?
From previou point we find that we have only one parameter lpThreadParameter.
Use the Strings window to locate the string \cmd.exe /c in the disassembly. Where is it located?
from view > Open subviews > strings then use search to find string here you find that location is 0x10095B34.

What is happening in the area of code that references \cmd.exe /c?
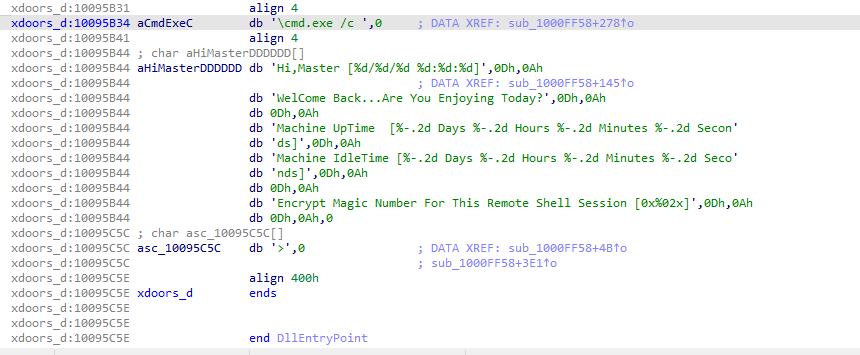 here we find that those strings are printed in consol window and those mainly referes to openning remot power shell
here we find that those strings are printed in consol window and those mainly referes to openning remot power shell
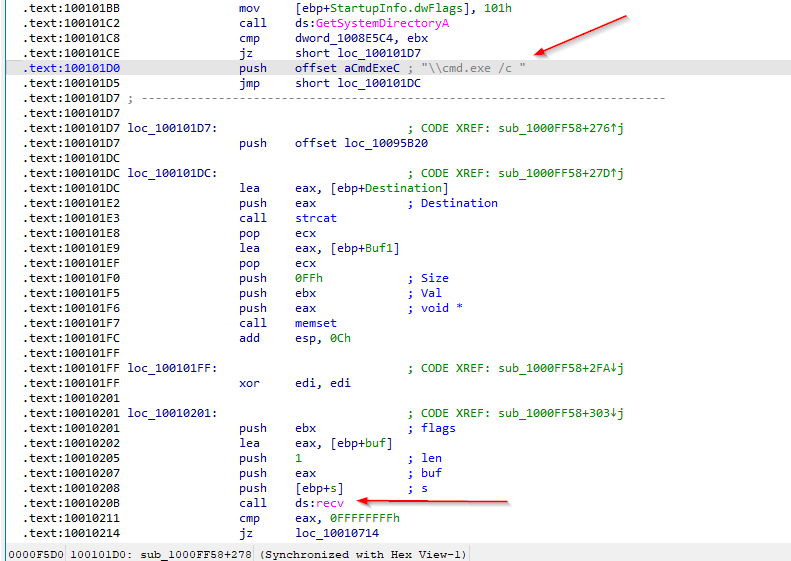
on checking the code at the offset we notice that cmd is pushed to stac then there is a call to recv fn those are also inddecators to the remote network connections.
In the same area, at 0x100101C8, it looks like dword_1008E5C4 is a global variable that helps decide which path to take. How does the malware set dword_1008E5C4?
Jumping to address we found XREF so let’s use our magic table
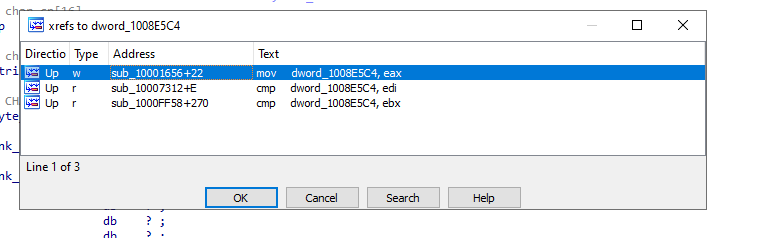
here we find it was calld 3 times one with mov instruction and 2 with cmp jumping to mov address we find a call instruction just before our move so let’s dive in this subrotine and find if there is a usefull data
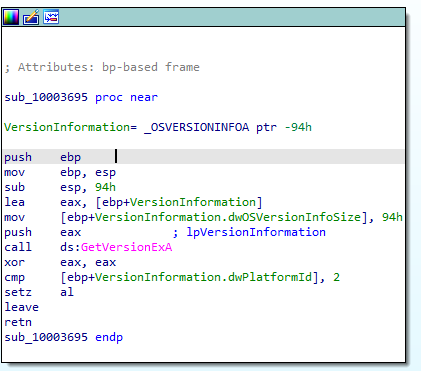
here its obvious that function check for OS version and return it so this value is stored at dword_1008E5C4.
A few hundred lines into the subroutine at 0x1000FF58, a series of comparisons use memcmp to compare strings. What happens if the string comparison to robotwork is successful (when memcmp returns 0)?
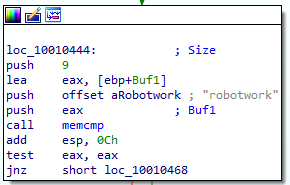
here we find our comparison, if the comparison is successful (memcmp returns 0) the test instruction will set ZF to 1 then the jump won’t happen and it will go to subrotine sub_100052A2
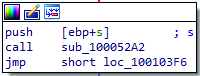
diving in this rotine we find comparison for two keys first “SOFTWARE\Microsoft\Windows\CurrentVersion” is being pushed then comparison is held at eax
after passing this comparison it checks for “WorkTime” then for “WorkTimes” so it checks for –> SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTime –> SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTimes
What does the export PSLIST do?
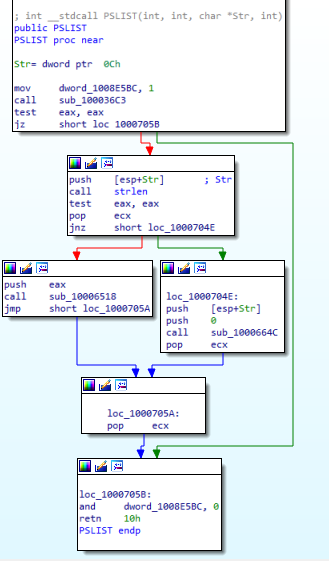
here it can return with information about running process (sub_100036C3) or any other specified process (sub_1000664C,sub_10006518)
Use the graph mode to graph the cross-references from sub_10004E79. Which API functions could be called by entering this function? Based on the API functions alone, what could you rename this function?
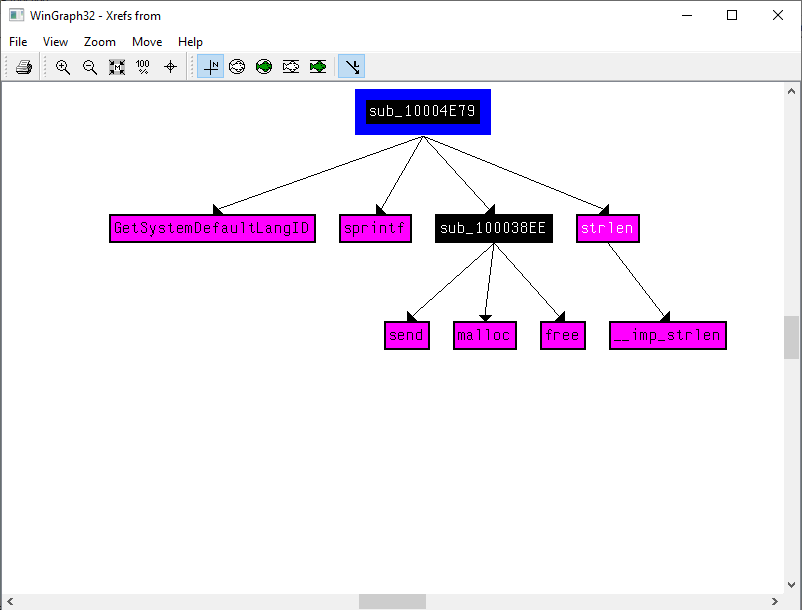
The API functions that can be called from these functions are:
1.GetSystemDefaultLangID 2.sprintf 3.strlen 4.send 5.malloc 6.free 7.__imp_strlen
based on previous analysis we have doubt that there is a power shell so send function maybe transfering some data from the system via this power shell and presence of GetSystemDefaultLangID is leading us to recognize that data is our OS language so we can rename function to be “Send Sys lang”.
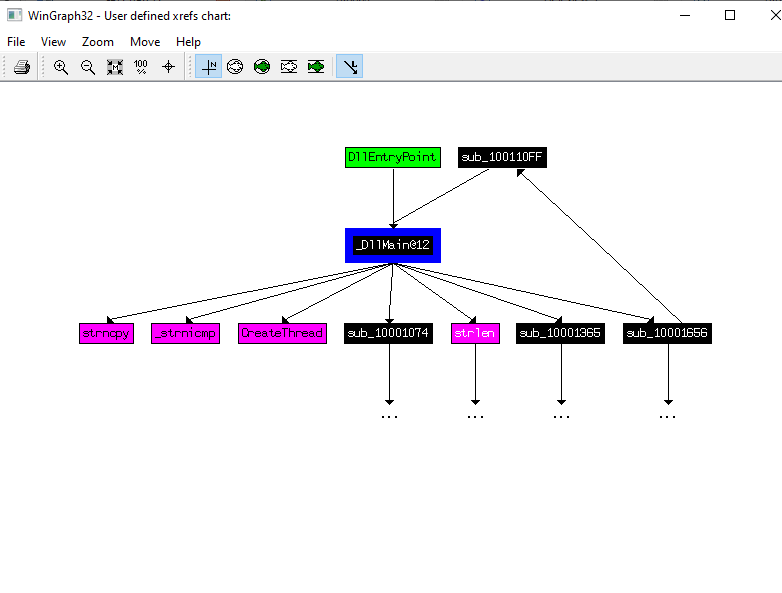
How many Windows API functions does DllMain call directly? How many at a depth of 2?
from View > Graphs > User Xref chart…
set depth to 1 you find
set depth to 2 you find
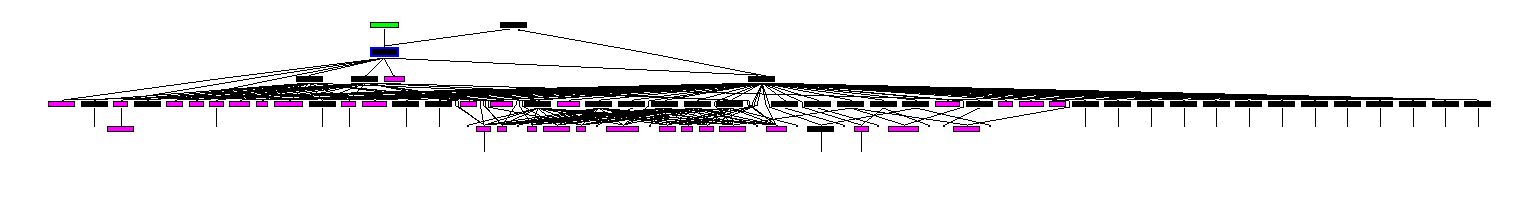
at depth 1 there is 4 functions that being called directly at depth 2 there is a huge number that cant be count if you are busy ;) but I have time so I count them 31 function at level 2.
At 0x10001358, there is a call to Sleep (an API function that takes one parameter containing the number of milliseconds to sleep). Looking backward through the code, how long will the program sleep if this code executes?
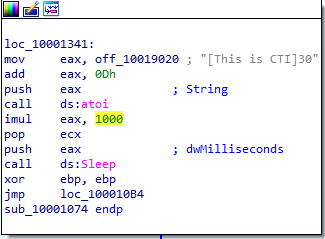
here there are many instructioins before sleep but the eax is pushed to our little function so we find its set to value at offset_10019020 so let’s figure out whats hidden in this black box I found that “[This is CTI]30” which will result 30 then eax is multiplied by 1000 so now eax stores 30000 which means that it will sleep for 30 secondes.
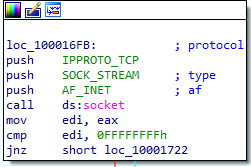
At 0x10001701 is a call to socket. What are the three parameters?
here some values are pushed for socket
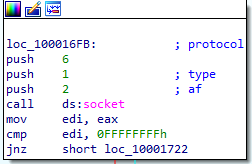
Using the MSDN page for socket and the named symbolic constants functionality in IDA Pro, can you make the parameters more meaningful? What are the parameters after you apply changes?
Search for usage of the in instruction (opcode 0xED). This instruction is used with a magic string VMXh to perform VMware detection. Is that in use in this malware? Using the cross-references to the function that executes the in instruction, is there further evidence of VMware detection?
searching for Sequence of bytes(or you can use text also) we found that

on doing some search for this instruction we find that

and find also that instruction Copies the value from the I/O port specified with the second operand (source operand) to the destination operand (first operand). The source operand can be a byte-immediate or the DX register; the destination operand can be register AL, AX, or EAX, depending on the size of the port being accessed (8, 16, or 32 bits, respectively). Using the DX register as a source operand allows I/O port addresses from 0 to 65,535 to be accessed; using a byte immediate allows I/O port addresses 0 to 255 to be accessed.
using xref graph

jumping to caller found
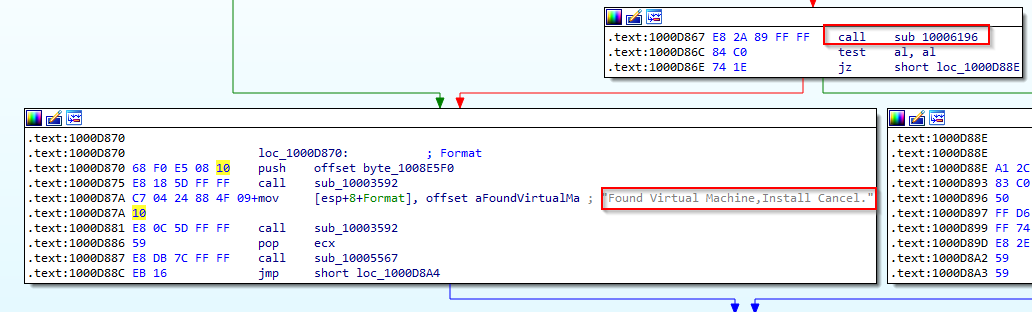
here we can finally conclude that it’s anti-Virtual machine mechanism, if your are runnig inside VM stop installation.
Jump your cursor to 0x1001D988. What do you find?
here we find some random data
Tools used :
- IDAFREE-7.7