IcedID
IcedId
Basic Analysis
IcedID is a PE32+ executable (DLL) (native) x86-64, for MS Windows
It kinda has no interesting strings except some sort of increased strings and URLs:
http://crl.comodoca.com/AAACertificateServices.crl04
http://ocsp.comodoca.com0
http://crl.sectigo.com/SectigoPublicCodeSigningRootR46.crl0
http://crt.sectigo.com/SectigoPublicCodeSigningRootR46.p7c0#
http://ocsp.sectigo.com0
https://sectigo.com/CPS0
http://crl.sectigo.com/SectigoPublicCodeSigningCAR36.crl0y
http://crl.sectigo.com/SectigoPublicCodeSigningCAR36.crl0y
http://ocsp.sectigo.com0
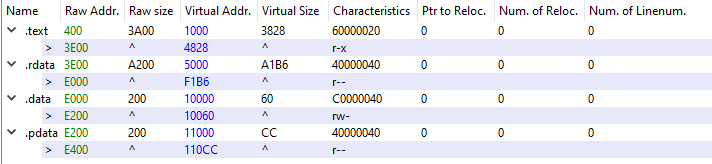
It is unpacked with four sections and six imported API as noticed from PE-bear.
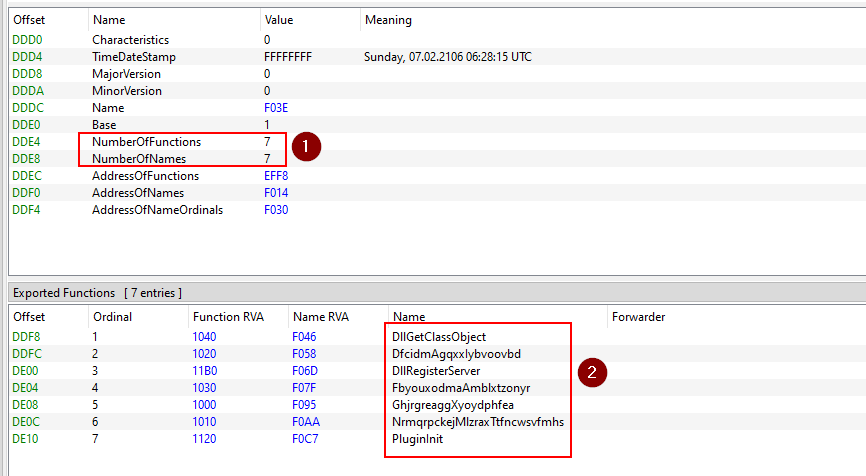
It also has Exports, it -as dll- exports 7 funcs:
now I assume it will drop another file which has bad code as these imports can only be used for something like thread injection.
Now it is IDA time.
Advanced Analysis
Static
At the entry point, there was nothing useful so I started to check its exported functions (mentioned before).
first one was DllGetClassObject which only performs two function calls:
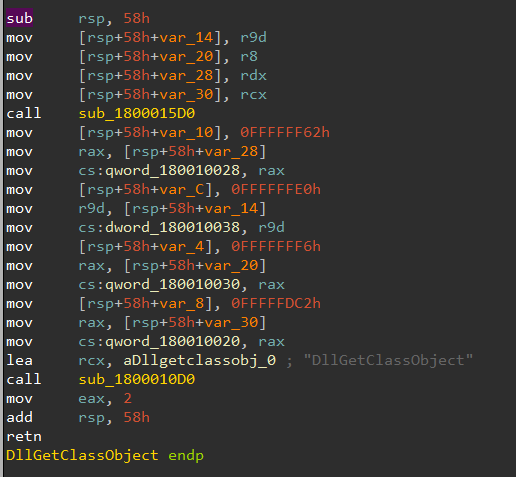
Both perform some arithmetic and XORing with 3 nested calls so I decided to leave it for now as it doesn’t seem interesting.
second on DfcidmAgqxxIybvoovbd only returns three.
third one DllRegisterServer performs the most interesting part for me:
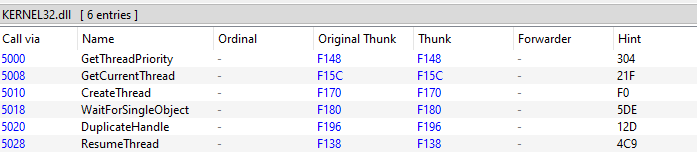
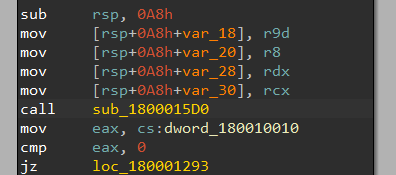 I noticed before that it only imports KERNEL32.dll which doesn’t make sense, so it must be hiding API calls.
The function starts with a call to a function that seems to be performing some dll resolving then it returns.
After that, it starts to check the thread which will be a preparation for some injection then performs a call to function
I noticed before that it only imports KERNEL32.dll which doesn’t make sense, so it must be hiding API calls.
The function starts with a call to a function that seems to be performing some dll resolving then it returns.
After that, it starts to check the thread which will be a preparation for some injection then performs a call to function sub_1800010D0:
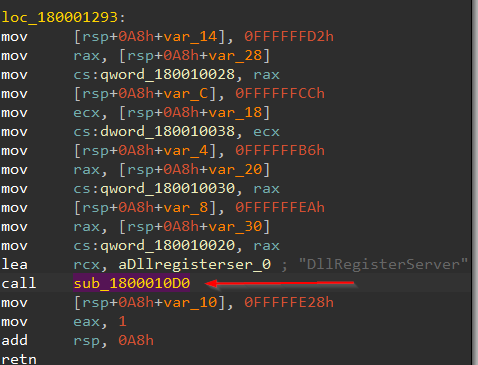
entering that sub found 2 sub-calls nearly do the same thing which is some prologue then call to r10 which is dynamically resolved:
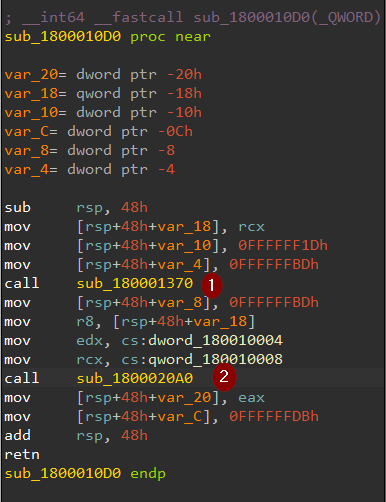
so now I know that I will start my debugging at DllRegisterServer, especially in that subroutine.
let’s have a quick look at other exports, they were empty except PluginInit which had 2 calls and seems to perform some runtime decryption as well.
Dynamic
I will use X64 this time, so at first, I load dll and then transfer the origin to DllRegisterServer and now I start stepping, in DllRegisterServer I will first check for my dll resolving assumption so entering the first call stepping until the first call which takes place in a loop as well found that it returns “AcquireSRWLockShared”.
now with a small trick, I can print all of the imported functions at the log screen by setting a conditional BP at that call:
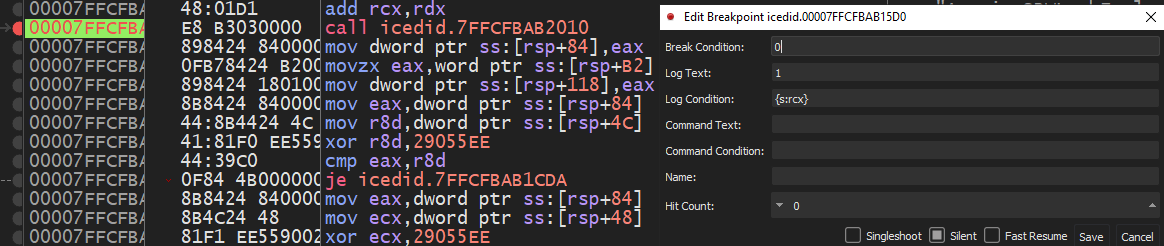
now all APIs are printed in the log screen I can check them as I want but now it’s more interesting to check our next call which is suspected to drop another file, the function arguments were passed as shown:
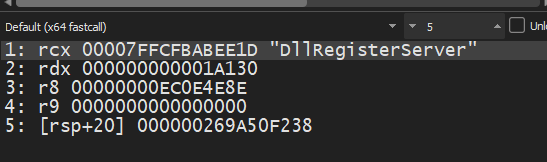
stepping into the first call as I mentioned before, I set BP at r10 call:
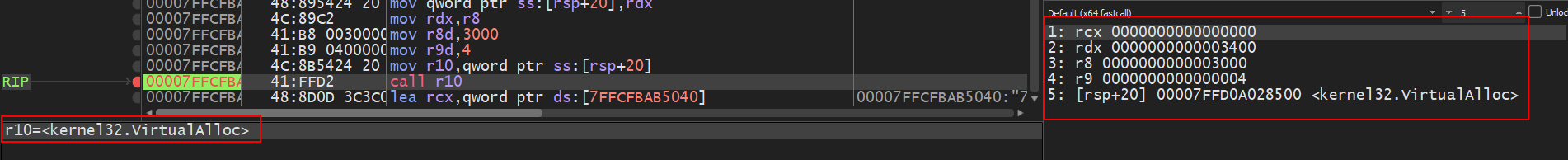
as you can see it will allocate virtual memory so the return value would be a memory start address stored in RAX, following in dump found that space is empty and there were only some calculations (seems to be decoding) then the value is assigned at this memory setting BP at the end of this process found that the memory is filled already with another code starting with mz header. I exported this file as a dump from X64 then repeated the same process with the second function and found it dropped another file so now I will start to analyse those 2 files.
IcedId_droped_1
Basic Analysis
IcedId_droped_1 is a PE32+ executable (DLL) (GUI) x86-64, for MS Windows.
From basic static analysis, there are no important strings only API calls & some cookie stuff:
__io=
Cookie: __gads=
%s%u
POST
_gat=
_u=
_gid=
_ga=
aws.amazon.com
Cookie: _s=
it’s also known that it’s fully unpacked.
from imports, it tries to reach out c2 server but first, it will use aws.amazon.com to ping the connection.
Advanced Analysis
Static
On opening EP found that there is only one nested call to CreateThread taking one interesting argument:
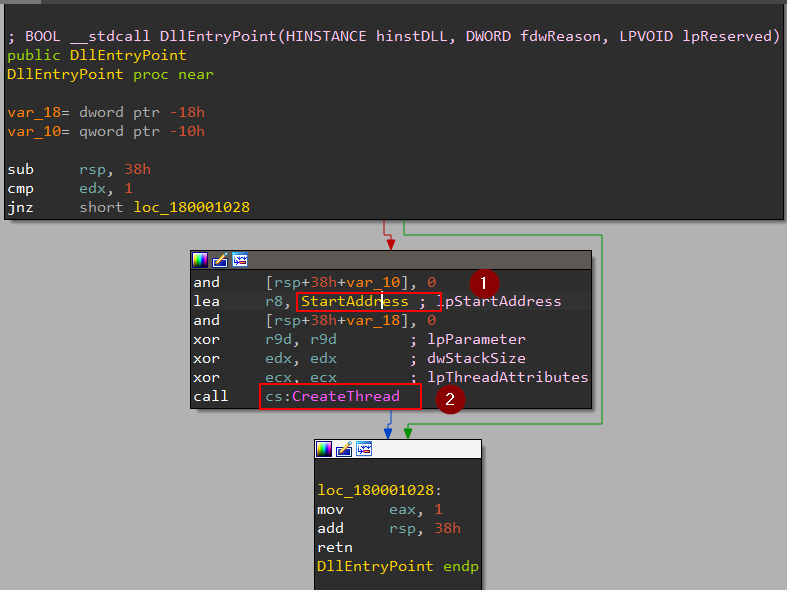
as you see we have a Long pointer to the start address where the code to be executed stored is passed to our API call to create the thread, so let’s dive into that address.
On entering that address found only one call we can consider as the main function, inside that main we find our code to be analysed so let’s start.
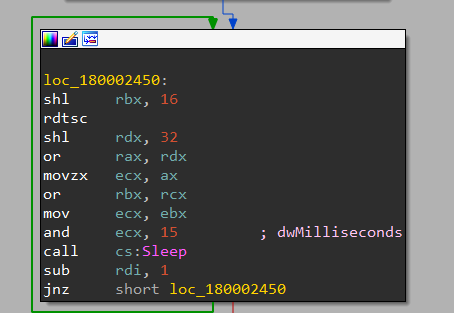
the first thing found is a sleep function which loops 5 times to evade sandboxes or behavioural analysis or at least annoy the analyst it will sleep for 26 milliseconds, next, there are three nested calls:
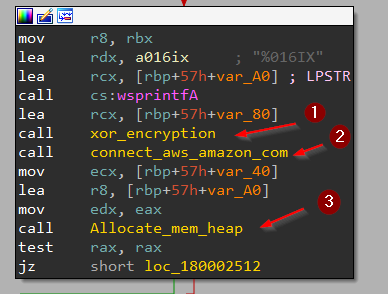
1 - The function performs only XOR for some data. 2 - it tries to connect to “aws.amazon.com” mentioned before in strings. 3 - Allocating Memory in the Heap and then performing some other calls which is an important function.
digging in function number three to see what it does after allocation found:
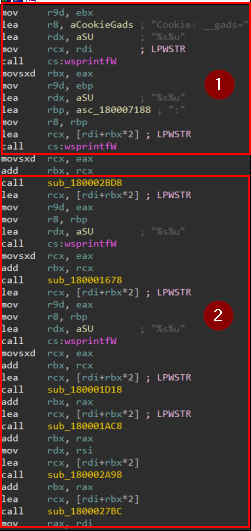
section n.1 creates a cookie and appends data to it using some buffer with a sprint API call, section n.2 performs some calls and then appends more information to that cookie so now o need to know what each performs.
sub_180002BD8: Retrieves the number of milliseconds that have elapsed since the system was started using theGetTickCount64API call, it’s used as an anti-analysis technique.sub_180001678: it keeps collecting system information usingZwQuerySystemInformationseems like it fingerprinting the system.sub_180001D18: keep the data collection up but this time with OS versionRtlGetVersion.sub_180001AC8: it has some calls that finally switch to another thread and then edit the cookie again.sub_180002A98: Here it collects computer and User names.sub_1800027BC: finally NIC information usingGetAdaptersInfo.
Note: All these calls perform some edits on our cookie. Now, after all these calls it returns a handle to allocated memory if it’s allocated correctly, it will continue executing, or else it will jump to the end.
now it’s time for the next main block where the connection is validated:
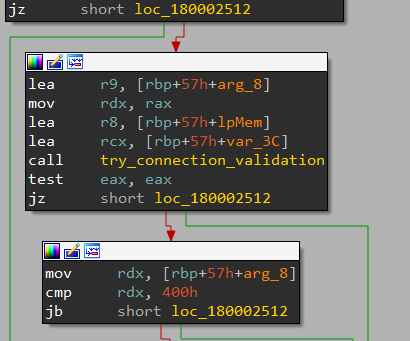
This one as it appears makes a call and then checks whether the return is zero (the connection failed) or not. In that function there is a nested call to a function it only prepares for HTTP connection and after return, it compares the return value with 404 which means that it checks if the page exists or not to gain control flow:
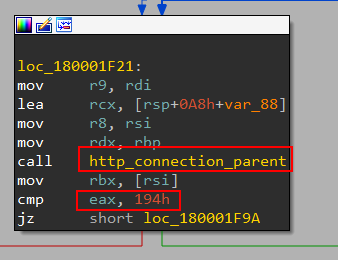
In http_connection_parent there is the call I mentioned to http_connection:
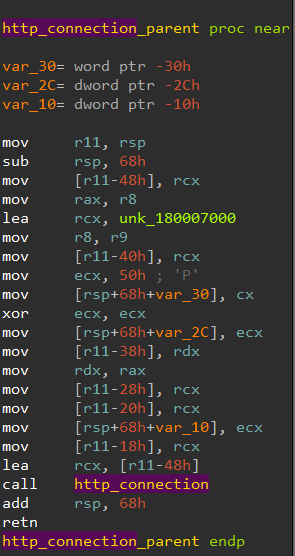
inside this function there are some API calls:
- WinHttpOpen:
- WinHttpSetStatusCallback:
- WinHttpConnect:
- WinHttpOpenRequest:
- WinHttpSetOption:
- WinHttpSendRequest:
- WinHttpReceiveResponse:
- WinHttpQueryHeaders:
- WinHttpQueryDataAvailable:
- WinHttpReadData:
- WinHttpCloseHandle:
these calls lead to a connection to the C2 server, using the X64 debugger found that C2 is solved in run-time and got the cookie value
Cookie: __gads=380132461:2:12306:117; _gat=10.0.1337.64; _ga=1.591594.2020557398.3223; _u=4445534B544F502D33414B454E4533:476F6C64656E:35393041383431344645413031413443; __io=21_2930852979_2098184808_4175261599; _gid=400849E87317
revedanstvy.bid
vedanstvy.bid
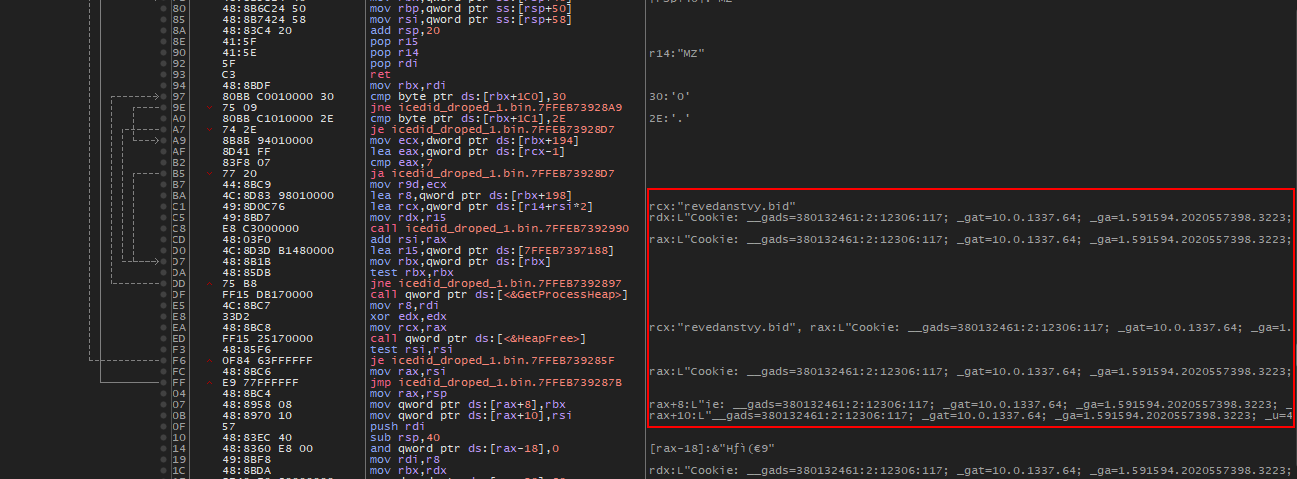
now it creates some file in the path “C:\Users\ *** \AppData\Roaming” it writes 0x30090 bytes from this “icedid_droped_1.bin.00007FFEC20D02C63”
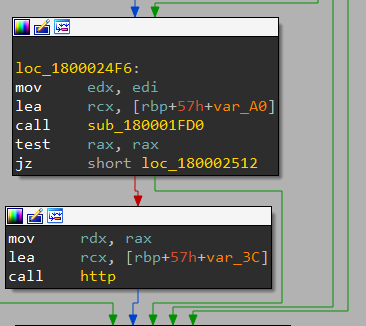
next one only make new cookie "Cookie: _s=:2147353476"
HTTP calls http_connection_parent one more time then terminate the program.
Conclusion
- As a conclusion this is a dropper which creates 2 other files.
- The dropped files perform the same thing.
- Steals data from the victim machine then send it to the C2 server.
capa
Main file —
| ATT&CK Tactic | ATT&CK Technique |
|---|---|
| EXECUTION | Shared Modules [T1129] |
| MBC Objective | MBC Behavior |
|---|---|
| PROCESS | Create Thread [C0038] |
| Resume Thread [C0054] |
| CAPABILITY | NAMESPACE |
|---|---|
| authenticate HMAC | data-manipulation/hmac |
| create thread | host-interaction/thread/create |
| resume thread | host-interaction/thread/resume |
| access PEB ldr_data | linking/runtime-linking |
| parse PE exports | load-code/pe |
| parse PE header (5 matches) | load-code/pe |
file n.1
| md5 | c1dd6f3d2c3ee21ebb4d3e93b74cab74 |
| sha1 | 2fc6f0c1003d03f3fe8cab1a4c617e9bbb0eb18c |
| sha256 | 9ff5c9ce0d1536ce8b043b10758453e3349a82cc31195ca57250a272e65b4da4 |
| path | icedid_droped_1.bin.dll |
| ATT&CK Tactic | ATT&CK Technique |
|---|---|
| DEFENSE EVASION | Obfuscated Files or Information [T1027] |
| Account Discovery [T1087] | |
| File and Directory Discovery [T1083] | |
| System Information Discovery [T1082] | |
| System Owner/User Discovery [T1033] | |
| EXECUTION | Shared Modules [T1129] |
| MBC Objective | MBC Behavior |
|---|---|
| ANTI-BEHAVIORAL ANALYSIS | Debugger Detection::Anti-debugging Instructions [B0001.034] |
| COMMUNICATION | HTTP Communication::Create Request [C0002.012] |
| HTTP Communication::Get Response [C0002.017] | |
| HTTP Communication::Read Header [C0002.014] | |
| HTTP Communication::WinHTTP [C0002.008] | |
| DATA | Encoding::XOR [C0026.002] |
| Non-Cryptographic Hash::FNV [C0030.005] | |
| DEFENSE EVASION | Obfuscated Files or Information::Encoding-Standard Algorithm [E1027.m02] |
| FILE SYSTEM | Create Directory [C0046] |
| Write File [C0052] | |
| PROCESS | Create Thread [C0038] |
| Terminate Process [C0018] |
| CAPABILITY | NAMESPACE |
|---|---|
| execute anti-debugging instructions (2 matches) | anti-analysis/anti-debugging/debugger-detection |
| initialize WinHTTP library | communication/http |
| read HTTP header | communication/http |
| prepare HTTP request | communication/http/client |
| receive HTTP response | communication/http/client |
| encode data using XOR (2 matches) | data-manipulation/encoding/xor |
| hash data using fnv | data-manipulation/hashing/fnv |
| get common file path (3 matches) | host-interaction/file-system |
| create directory | host-interaction/file-system/create |
| write file (2 matches) | host-interaction/file-system/write |
| get hostname (2 matches) | host-interaction/os/hostname |
| terminate process | host-interaction/process/terminate |
| get session user name | host-interaction/session |
| get user security identifier (2 matches) | host-interaction/sid |
| create thread | host-interaction/thread/create |
| link function at runtime (5 matches) | linking/runtime-linking |
| parse PE header | load-code/pe |
file n.2
no capabilities found
IOCs
33cc3816f98fa22354559711326a5ce1352d819c180be4328a72618d20a78632
9ff5c9ce0d1536ce8b043b10758453e3349a82cc31195ca57250a272e65b4da4
41a6f3c590ea10c7e3d3d9b31dbcb0f0477aa39e2e4948b2b5619961a7708295
revedanstvy.bid
vedanstvy.bid
Cookie: _s=:2147353476
Cookie: __gads=380132461:2:12306:117; _gat=10.0.1337.64; _ga=1.591594.2020557398.3223; _u=4445534B544F502D33414B454E4533:476F6C64656E:35393041383431344645413031413443; __io=21_2930852979_2098184808_4175261599; _gid=400849E87317
tools
- PE-bear
- peid & KANAL plugin
- floss.exe
- IDA
- capa plugin
- hashdp plugin